Defenseless memcached servers still face the web as they were ever meant to.
DDoS amplification methods are pursued by the bad guys for a long time. Hitting the weakest point of the hosting chain is a way. Leveraging a service widely used in many web-facing servers in order to generate traffic is another.

From memcached’s Wiki:
By default memcached listens on TCP and UDP ports, both 11211.
-lallows you to bind to specific interfaces or IP addresses. Memcached does not spend much, if any, effort in ensuring its defensibility from random internet connections. So you must not expose memcached directly to the internet, or otherwise any untrusted users. Using SASL authentication here helps, but should not be totally trusted.
By spoofing an IP address in a UDP connection, an attacker can efficiently carry a DDoS attack just by stacking the memcached “stats” command:
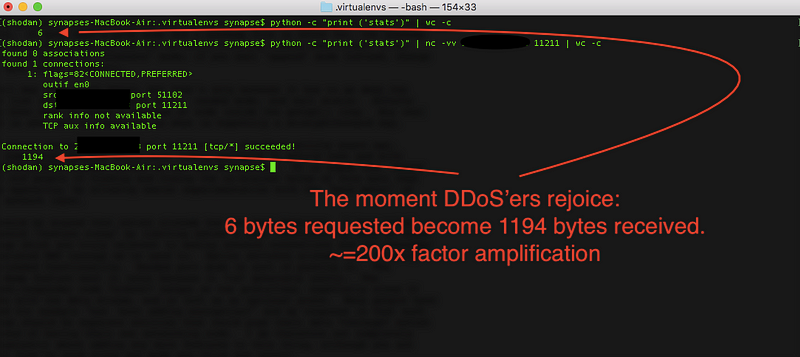
keep the stats\nstats\nstats\nstats going…
So how’s the real world doing?
Bad.
So how’s this tiny South American country doing?
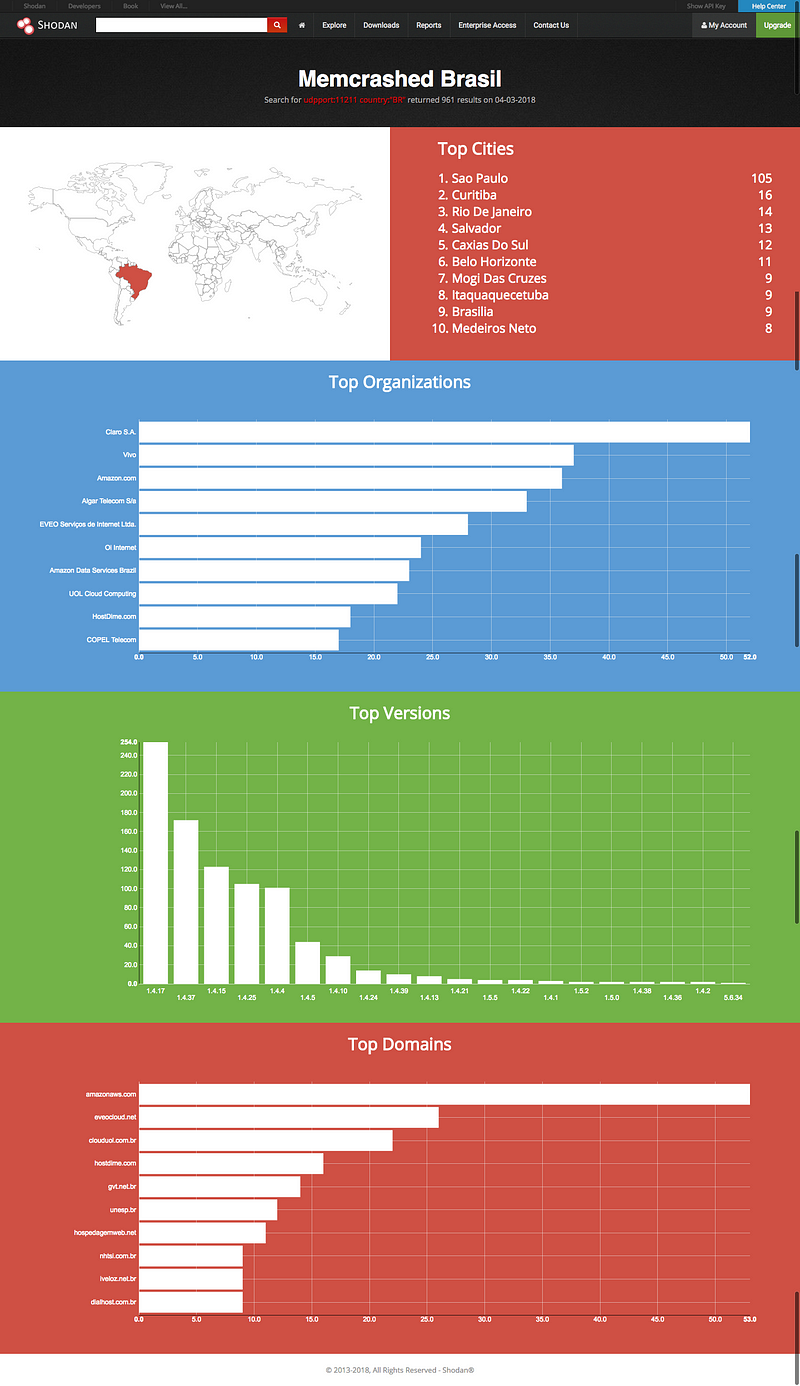
obligatory Shodan report.
Take another look at the top versions graph.
More than half of the servers (which shouldn’t be exposed to the web) run versions outdated and prone to RCE vulnerabilities reported by Talos in 2016. Which can result in crafted requests to efficiently maximize the amplification factor of the DDoS attack as described in the 0kee report.
Update memcached.